Modern vehicles are essentially computers on wheels, with dozens of Electronic Control Units (ECUs) and millions of lines of software code. This connectivity, from GPS and infotainment to V2X and over-the-air updates, makes automotive cybersecurity critical. Hackers can target vehicle networks to steal personal data or even hijack vehicle controls. A dedicated Security Operations Center (SOC) for automotive systems continuously monitors vehicle traffic, telematics servers, and cloud services 24/7 to detect and respond to these threats in real time. In this article, we explain what an automotive SOC does, why it’s essential for modern vehicles, and the key benefits it provides.
What is a SOC in Automotive Cybersecurity?
A Security Operations Center (SOC) is a centralized team and platform for monitoring and managing security threats. In the automotive world, a Vehicle SOC (VSOC) extends this concept to cars and connected mobility. According to security experts, “a SOC is a team that deals with security issues” at a technical level, using dedicated tools to constantly monitor an organization’s IT and network infrastructure. A Vehicle SOC does the same but also watches over the car-specific components – everything from the connected vehicle cloud and fleet management systems to the vehicles themselves, including on-board sensors and radars. In effect, an automotive SOC acts as the cybersecurity command center for a manufacturer or fleet, aggregating data from vehicle ECUs, telematics units, and cloud services to detect anomalies and incidents.
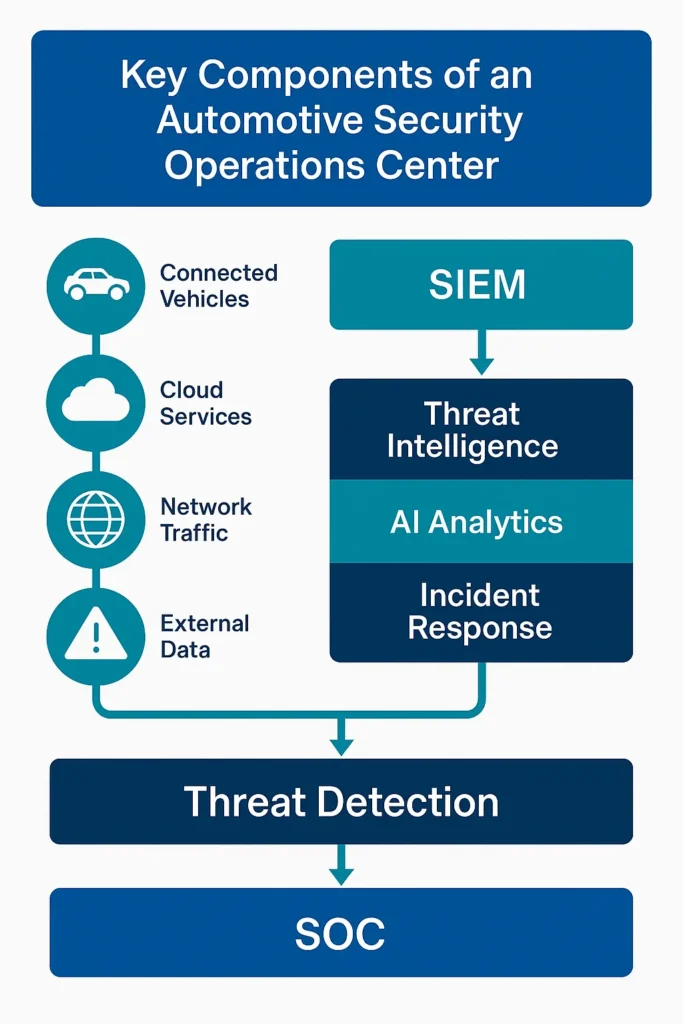
The diagram above illustrates a typical SOC architecture. A SOC ingests data logs (from ECUs, on-board networks, and cloud connectors), aggregates and correlates events, and applies threat intelligence. Security analysts or automated tools then triage alerts and trigger incident response actions. As Thales puts it, a SOC is “the command center for identifying emerging cybersecurity threats and responding immediately to mitigate risk”. By centralizing visibility across the entire connected vehicle ecosystem, a SOC can quickly spot malicious behavior, for example, abnormal network packets or unauthorized firmware changes, and contain them before they affect the vehicle or backend systems.
Cybersecurity Threats to Connected Vehicles
Today’s vehicles are “rolling data centers,” connected to multiple networks. This connectivity brings convenience but also exposes vehicles to cyberattacks. Common threats in the automotive landscape include:
- Vehicle Hacking: Attackers exploit vulnerabilities in ECUs or V2X (Vehicle-to-Everything) links to manipulate car functions (e.g., engine, brakes, or locks).
- Data Breaches: Personal information and telemetry data stored in cloud services or in-vehicle systems can be stolen or leaked.
- Ransomware Attacks: Cybercriminals may encrypt or lock down a vehicle’s systems (infotainment, telematics, etc.) and demand payment to restore access.
- Supply Chain Attacks: Malicious code can be introduced during software updates or through compromised components in the vehicle supply chain.
Kaspersky Security warns that if a hacker “remotely hijacks the operating system of one of your vehicles,” the consequences could be devastating. Given these risks, automotive manufacturers and fleet operators need robust monitoring and quick response capabilities. A SOC provides this 24/7 vigilance, acting like a security watchdog for every network and device in the connected car domain.
Key Benefits of SOC in Automotive Cybersecurity
Implementing an automotive SOC brings several important advantages:
- Continuous Threat Detection: A SOC continuously scans vehicle networks and cloud infrastructure for anomalies. Horizon Connect notes that an SOC service offers “round-the-clock monitoring to detect and respond to threats in real time”. This means suspicious signals in the data flow – like unusual commands sent to an ECU or abnormal login attempts – are caught immediately.
- Rapid Incident Response: When a threat is detected, the SOC team can act instantly to isolate and contain it. This might involve cutting off a hacked vehicle from the fleet network or rolling out an emergency update. Quick response “prevents downtime” and minimizes impact on drivers and manufacturers. Thales emphasizes that uninterrupted monitoring by an SOC “improves response times when security issues occur,” reducing damage and costs.
- Centralized Visibility: A dedicated automotive SOC provides a single pane of glass for the entire vehicle ecosystem. It correlates data from ECUs, mobile apps, infrastructure sensors, and more. By centralizing this visibility, it becomes much easier to spot patterns of attack that span multiple vehicles or systems. For example, an SOC can detect if a batch of cars suddenly tries to contact a suspicious IP address.
- Threat Intelligence & Analytics: Modern SOCs leverage AI and machine learning to predict and prevent attacks. As Horizon Connect highlights, SOC platforms use “AI-driven analytics to predict and neutralize attacks before they occur”. This proactive intelligence is crucial for automotive cybersecurity, where new malware or attack methods can emerge rapidly.
- Regulatory Compliance: Many countries now mandate automotive cybersecurity standards (e.g., UNECE WP.29, ISO/SAE 21434). A SOC helps meet these requirements by continuously monitoring and documenting cyber risks. Detailed reporting from a SOC makes it easier to show regulators that security measures are in place and up-to-date.
These benefits make a SOC a foundational element of a mature automotive cybersecurity strategy. Figure [11] (above) highlights components like log collection, Security Information and Event Management (SIEM), and threat intelligence feeds that together enable these capabilities.
Implementing an Automotive SOC
Building an effective Vehicle SOC can be done in-house or by outsourcing to experts. Some large OEMs and fleet operators establish their own VSOCs, while others partner with specialized cybersecurity firms (offering “SOC as a Service”). Regardless of the approach, key steps include:
- Integrate Vehicle Data Streams: Ensure that all vehicle and network logs (from telematics, diagnostic sensors, mobile apps, etc.) feed into the SOC’s monitoring platform. This may involve deploying onboard intrusion detection systems or cloud agents to collect telemetry.
- Develop Incident Playbooks: Prepare response procedures for different scenarios (e.g., remote takeover attempts, data breach, malware outbreak). Analysts should know how to escalate issues and whom to notify in each case. As one expert notes, escalating vehicle monitoring alerts straight to the SOC is critical for quick remediation.
- Leverage Threat Intelligence: Subscribe to multiple threat feeds (from industry groups, security vendors, etc.) and continuously update the SOC’s knowledge base. Correlating external intelligence with vehicle behavior helps spot known attack patterns.
- Regular Training and Testing: SOC analysts need specialized training on automotive systems, which differ from IT networks. Regular drills and penetration tests (e.g., red-team exercises on vehicles) help ensure the SOC is ready. Horizon Connect also recommends fuzz testing and white-hat hacking programs to find vulnerabilities before adversaries do.
In some cases, vehicles can even report their own issues to the SOC. For example, onboard modules might automatically flag unusual commands or sensor readings back to the SOC dashboard. This feeds the SOC with richer data to analyze. Ultimately, whether run internally or by a vendor, the goal of the SOC is the same: “minimize the chances of a cybersecurity breach” across your entire fleet, so engineers can focus on building the future of transport.
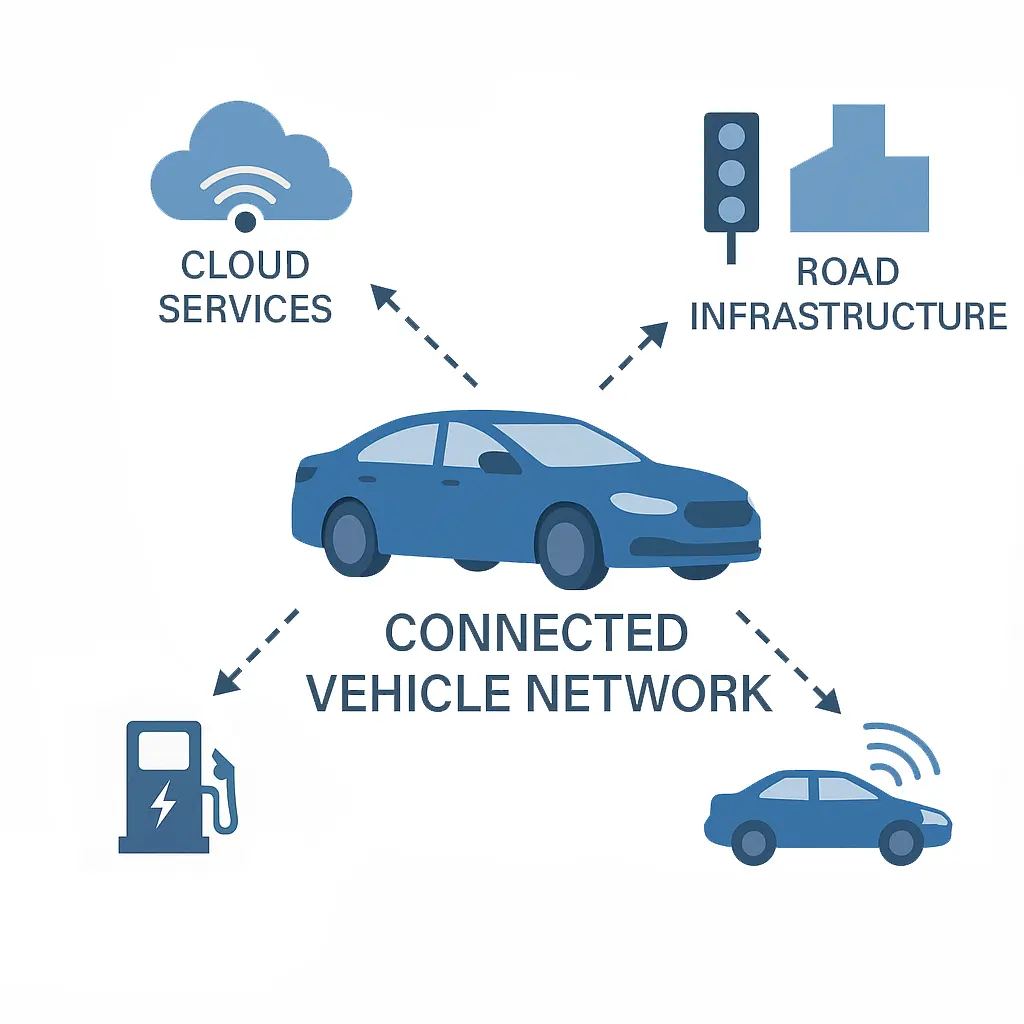
The graphic above illustrates a typical connected vehicle ecosystem. Each interface (cellular, V2X, OTA updates, Bluetooth) can be an entry point for attackers. A SOC in automotive cybersecurity monitors all these links and internal vehicle networks. For instance, if a car’s infotainment unit suddenly transmits data to an unknown server, the SOC would generate an alert for analysts to investigate. By correlating data from hundreds or thousands of vehicles, the SOC can identify even subtle threats (such as malware that only activates under certain conditions).
Conclusion
As vehicles become increasingly software-driven and networked, SOCs are no longer optional – they are essential for keeping drivers and data safe. A well-designed Security Operations Center provides continuous oversight of car networks, enabling fast threat detection, incident response, and compliance with evolving regulations. Horizon Connect specializes in automotive SOC solutions and offers SOC-as-a-Service to help manufacturers and fleet operators protect their connected vehicles. By integrating advanced monitoring, managed detection, and proactive vulnerability management, we ensure the automotive industry can “drive forward securely,” safeguarding both passengers and data.